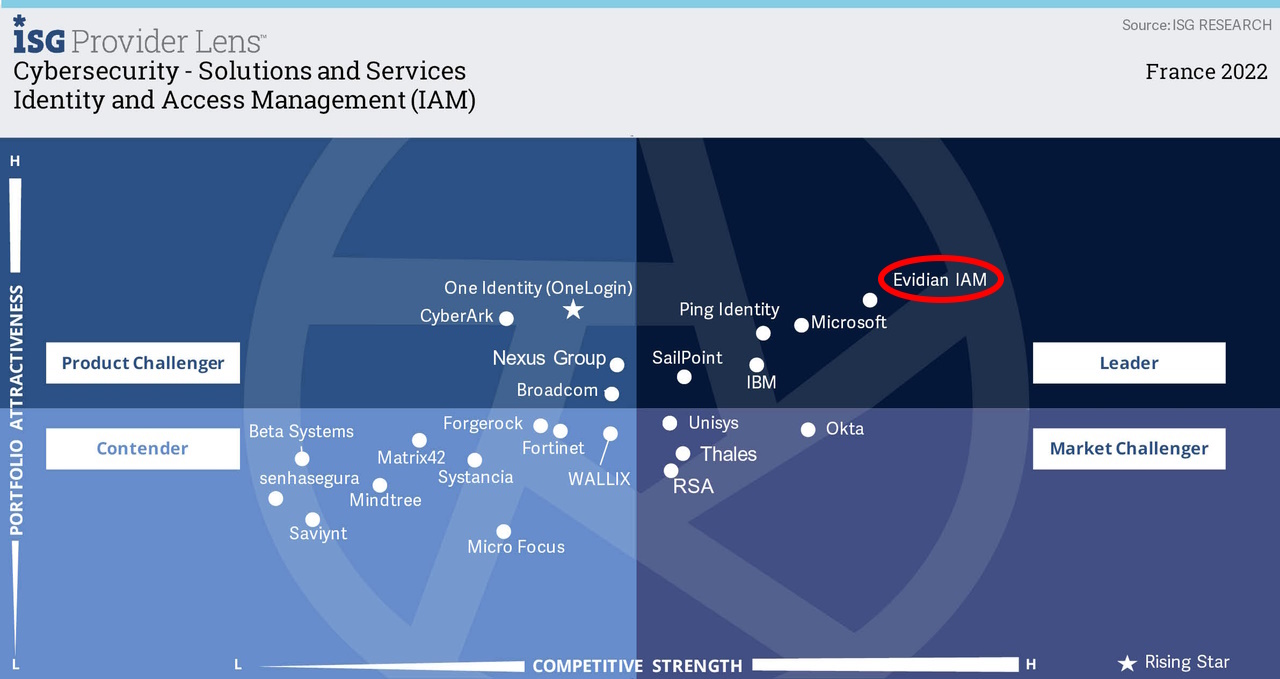
Consulting
Evidian provides a series of IAM consulting services to help you build your identity and access management project. These services cover three principle domains:
- Implementation/demonstrator's assistance with implementation/model
- Advice and audit services
- Design: technical architecture with the constraints of high availability (IT safety plan), detailed IAM functional specifications (workflow, policy, upstream and downstream provisioning), SSO and strong authentication, Web SSO
Demonstration
For our E-SSO & Authentication Manager, WAM, IAM and SafeKit products, Evidian offers to implement a POC (Proof of concept)
| Prerequisites |
|
| Participants |
|
| Content |
|
| Equipment |
|
Design
Evidian offers you support in the design phase of your project using our E-SSO & Authentication Manager, WAM, IAM and SafeKit products.
Here are some examples of tasks that can be achieved in Evidian:
|
Task |
Content |
| ESSO technical and functional specifications |
|
| WAM technical and functional specifications |
|
| IAM technical and functional specifications |
|
Advice & Audit
The advice and audit group offers to support you with:
- Preparation studies
- Defining the project (outline, project plan, WBS)
- The design stages of the identity and access management solution
We will spend time specifically on considering the organisational and technical aspects of such projects, and the ROI: financial, for users, professionals, IT support teams and of course security teams (implemented from an SMSI, professional regulatory constraints: Bale II/III, Solvency, HIPAA).
With regard to audit, the methodology adopted is the following:
Here are some examples of consulting tasks that can be achieved in Evidian:
|
Task |
Content |
| Audit of the existing set-up |
|
| Proposing a management model for the organisation's authorisations with Policy Manager |
|
| Needs assessment in terms of strong authentication |
|
Expert testimony
Issue
A major player in the aeronautical sector, let's call it X, decided to provide shared access for all its branches and divisions. At the same time, X had set up a private cloud to store the access portal and shared services. To facilitate access to these services, X wished to offer a Single Sign-On service to its users, and extend this service to all its divisions.
X wanted to simplify the authentication process for users to access the "cloud", which had to comply with four successive authentications at the time.
Our proposal
We analysed the existing portal
It was a web application installed in the "cloud", federating access to all divisions, and allowing access to the shared resources of the company. The "cloud" contributed to direct access to shared services such as the CRM, intranet applications, HR, etc.
Choosing the right technical solutions
- E-SSO (Enterprise SSO): An SSO device is installed on each workstation. Whenever the user enters a login/password, the SSO remembers it locally. After the user has successfully logged on, the SSO agent waits for the application's login request. It intercepts those requests and automatically fills in the fields.
- Web SSO: Web SSO is an extension of the E-SSO device, designed specifically for web applications. A web portal is the interface between the client and the applications.
- SSO federation:
Analysing each scenario
- Scenario 1: Using E-SSO for various divisions
- Scenario 2: Using WAM for the main portal and offering E-SSO as an option
- Scenario 3: Integrating the access portal into the WAM and offering E-SSO as an option
Analysing the costs: in terms of equipment, licences and effort required to implement each scenario
Offering an analysis of the different scenarios: selection criteria, decision matrix, SWOT table
Orbion
Evidian takes care of everything related to your Identity and Access Management with Orbion (Identity as a Service)
Learn more >
Identity Governance and Administration
Manage access and authorization of all your users in your company
Learn more >
Web Access Manager
Gateway for web apps with SSO, multi-factor authentication, identity federation
Learn more >
Authentication Manager
Authentication Manager
Enterprise multi-factor & passwordless authentication on Windows PCs
Learn more >
Enterprise Single Sign-On (SSO)
Secure access to legacy and web apps on PCs & mobiles with SSO