Identity & Access Management:
avoiding binary choices
Sharing an IAM in a private Cloud
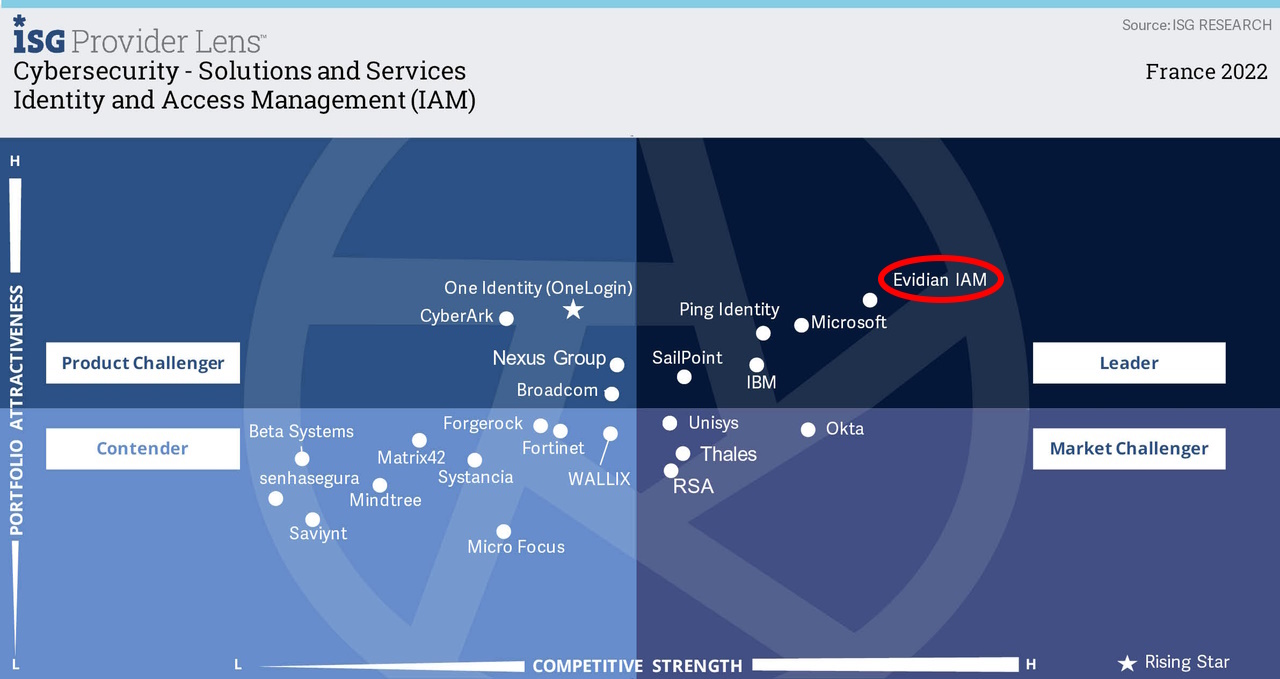
As a major editor of Identity & Access Management (IAM) solutions we are witnessing an increasing need for adaptive and agile delivery models in the IAM sector.
Today, organizational structures can be very complex. Large organizations are often split into separate business units which can operate very differently. To reduce costs and improve security and governance many organizations are now looking to harmonize processes across their entire business.
IAM for multi-entity groups: a new paradigm
In large groups, the smallest entities may not have the critical size to support in-house projects. The lack of human, technical and financial resources is the first hurdle for the implementation of IAM projects. ‘Classic’ on premise solutions can be too costly to acquire and own, and their implementation in every single entity would turn out to be overwhelming.
Today, one of the main IT trends is the shift from solutions hosted on premise to outsourced shared pools of configurable system resources and services, more commonly referred to as Software-as-a-Service (SaaS) or ‘Cloud’ solutions.
However, market experience and customer feedback has shown that many large companies haven’t made a decision yet when it comes to IAM. Many prefer to try to keep these services in-house to maintain control and worry about the lack of service levels from Cloud service providers.
A shared-services IAM solution is a “private Cloud” where the main advantage is that organizations only need to buy a unique license for a solution that is centrally hosted and administered. Capital expenditures are shared and operational expenses optimized.
Various degrees of freedom
This type of project is also able to meet the demands of individual business units by allowing some flexibility on governance and IT.
Depending on the degree of freedom the leading entity grants to its business units, it sets the degree of customization of the solution. The configuration scope can go from only shared machines and software to a fully configured IAM solution with strict governance and unique processes.
After defining the functional scope of the solution, the implementation team assesses the technical specifications for the physical architecture necessary to the project. The functional distinctions between subsidiaries and the degree of customization allowed will impact the identity, the application and entitlement attribution life-cycles as well as administrative function.
The goal at this stage is to ensure the long-term sustainability of the solution and avoid the technical debt that could derive from a too high level of customization. The success of a shared-services IAM project relies on strong governance and the full engagement of the main stakeholders across all entities. Capacity to execute must be optimal to harmonize processes and manage change.
An adaptive approach
This type of delivery model is not new but tends to be overlooked as SaaS IAM solutions are now on the market. It provides an answer when a completely outsourced solution doesn’t meet customers’ needs.
We can avoid binary choices and be more flexible with solutions that meet the needs of those who would want on premise solutions but need the scalable and adaptive approach of Cloud.