The solution for Kubernetes K3S
Evidian SafeKit brings high availability to Kubernetes K3S between two redundant servers. This article explains how to implement quickly a Kubernetes cluster on 2 nodes without NFS external storage, without an external configuration database and without specific skills.
Note that SafeKit is a generic product. You can implement with the same product real-time replication and failover of directories and services, databases, Docker, Podman, full Hyper-V or KVM virtual machines, Cloud applications (see all solutions).
This clustering solution is recognized as the simplest to implement by our customers and partners. The SafeKit solution is the perfect solution for running Kubernetes applications on premise and on 2 nodes.
We have chosen K3S as the Kubernetes engine because it is a lightweight solution for IoT & Edge computing.
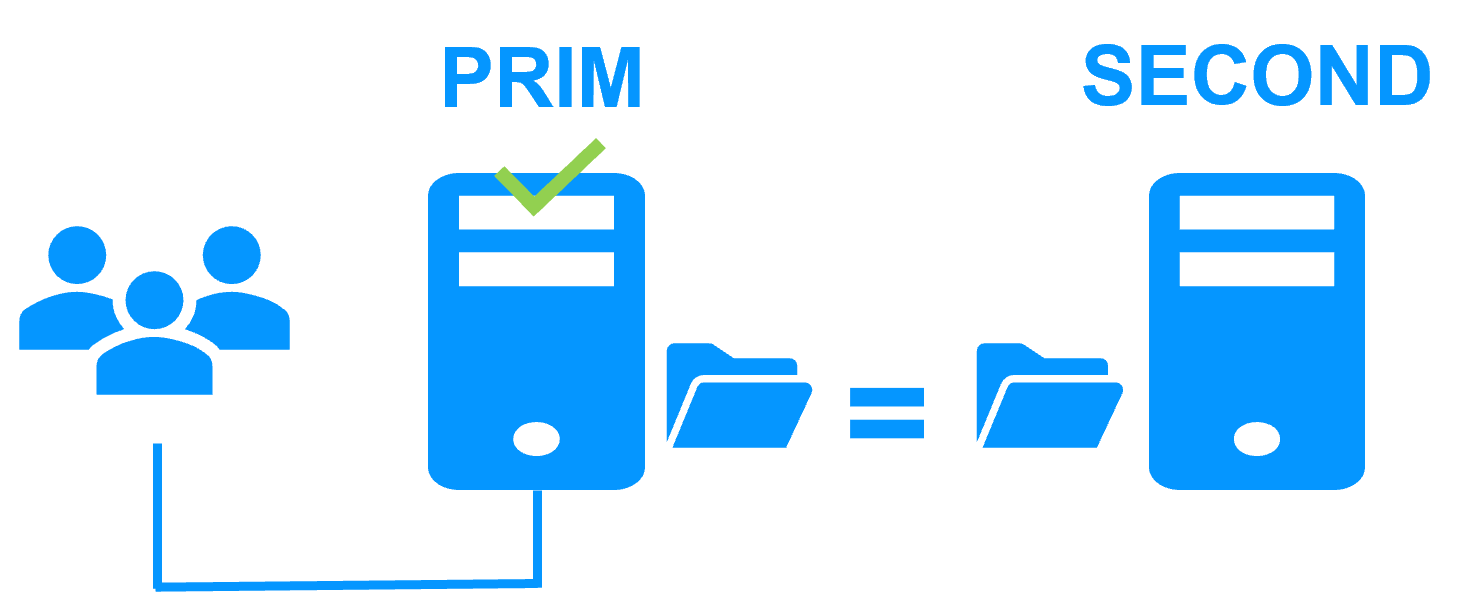
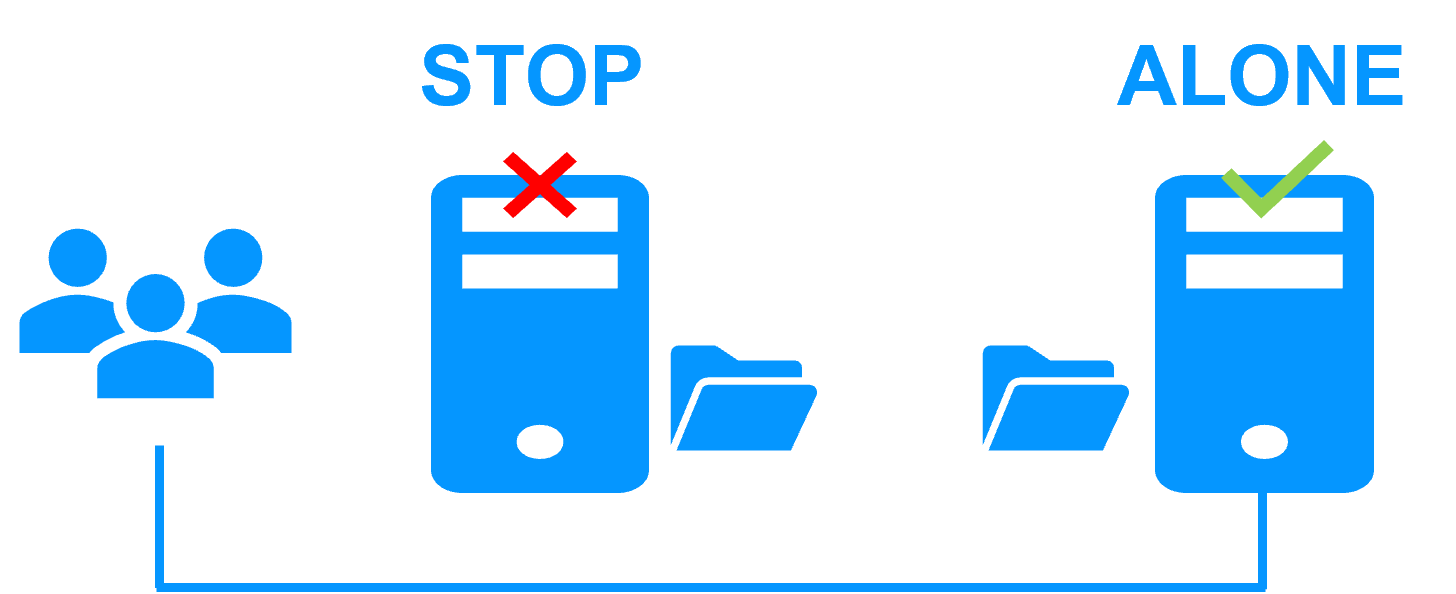
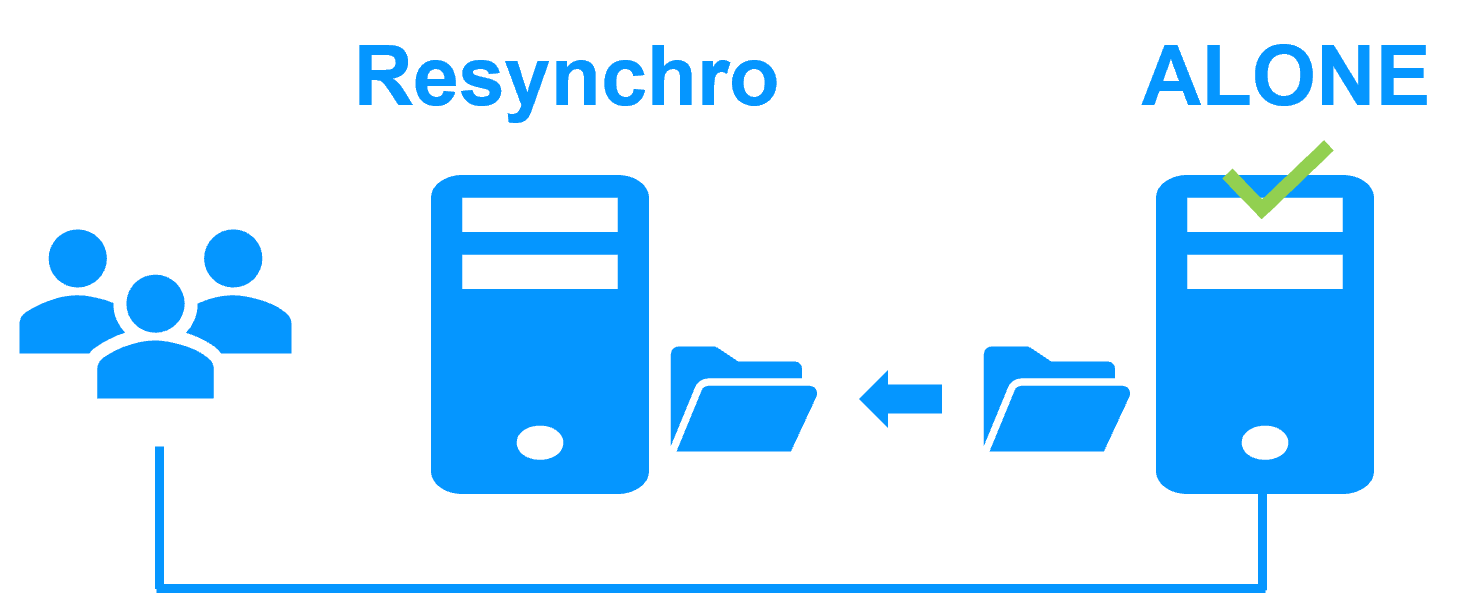
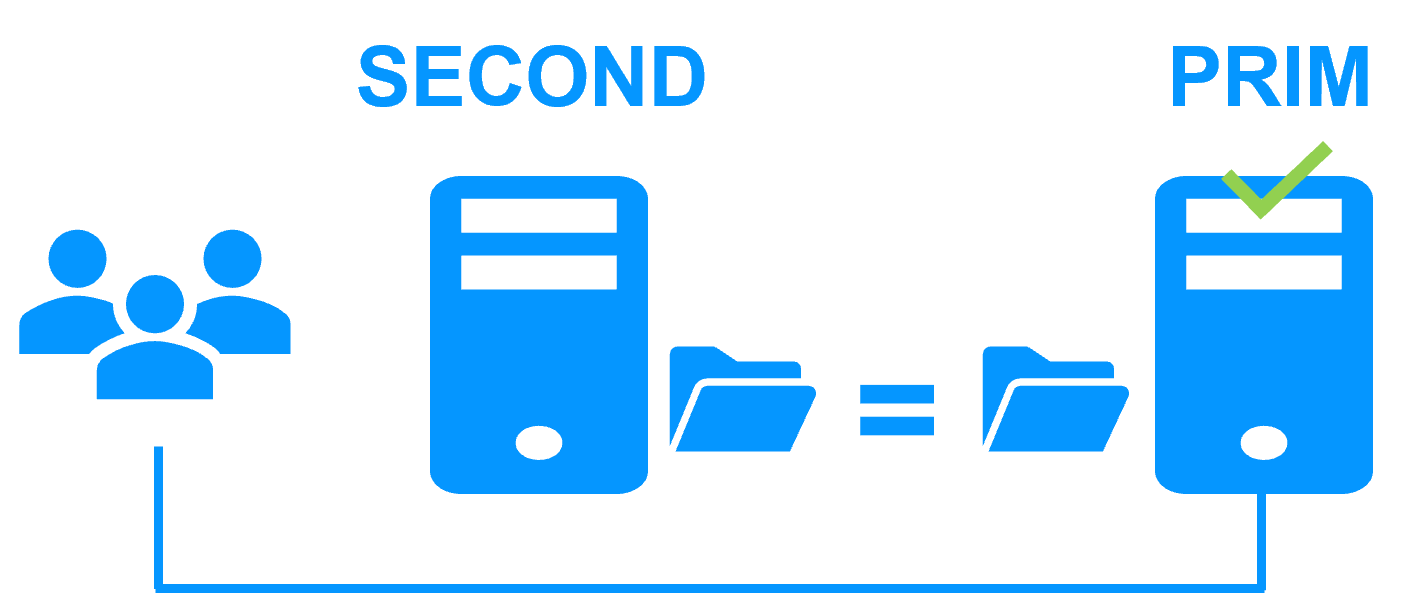
The k3s.safe mirror module implements:
- 2 active K3S masters/agents running pods
- replication of the K3S configuration database (MariaDB)
- replication of persistent volumes (implemented by NFS client dynamic provisionner storage class: nfs-client)
- virtual IP address, automatic failover, automatic failback