SafeKit Application Module Library: Ready-to-Use Solutions
This table presents the SafeKit High Availability (HA) solutions, categorized by application and operating environment (Databases, Web Servers, VMs, Cloud). Identify the specific pre‑configured .safe module (e.g., mirror.safe, farm.safe, and others) required for real‑time replication, load balancing, and automatic failover of critical business applications on Windows or Linux. Simplify your HA cluster setup with direct links to quick installation guides.
⚠️ Note: The .safe modules are available for download in the installation guides. A SafeKit .safe module is essentially a pre‑configured High Availability (HA) template that defines how a specific application will be clustered and protected by the SafeKit software. In practice, it contains a configuration file (userconfig.xml) and restart scripts.
| Application Category | HA Scenario (High Availability) | Technology / Product | .safe Module | Installation Guide |
|---|---|---|---|---|
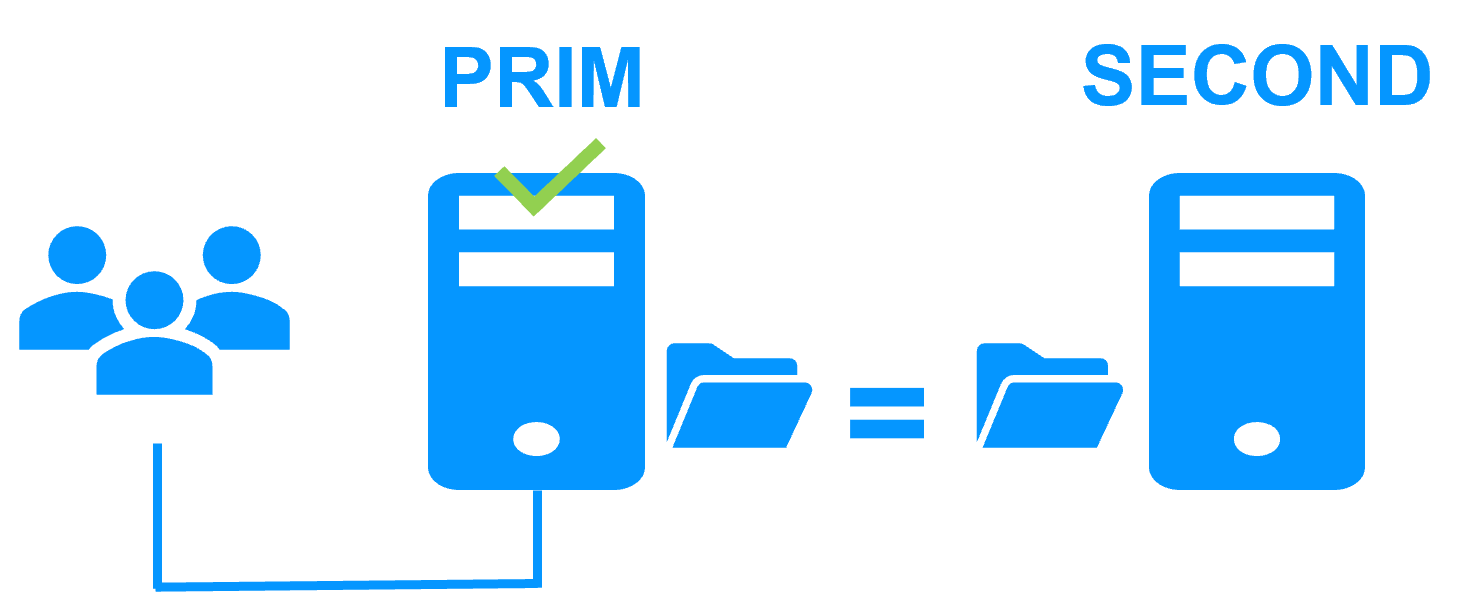
| New Applications | Real-Time Replication and Failover | Windows | mirror.safe |
View Guide: Windows Replication |
| New Applications | Real-Time Replication and Failover | Linux | mirror.safe |
View Guide: Linux Replication |
| New Applications | Network Load Balancing and Failover | Windows | farm.safe |
View Guide: Windows Load Balancing |
| New Applications | Network Load Balancing and Failover | Linux | farm.safe |
View Guide: Linux Load Balancing |
| Databases | Replication and Failover | Microsoft SQL Server | sqlserver.safe |
View Guide: SQL Server Cluster |
| Databases | Replication and Failover | PostgreSQL | postgresql.safe |
View Guide: PostgreSQL Replication |
| Databases | Replication and Failover | MySQL | mysql.safe |
View Guide: MySQL Cluster |
| Databases | Replication and Failover | Oracle | oracle.safe |
View Guide: Oracle Failover Cluster |
| Databases | Replication and Failover | Firebird | firebird.safe |
View Guide: Firebird HA |
| Web Servers | Load Balancing and Failover | Apache | apache_farm.safe |
View Guide: Apache Load Balancing |
| Web Servers | Load Balancing and Failover | IIS | iis_farm.safe |
View Guide: IIS Load Balancing |
| Web Servers | Load Balancing and Failover | NGINX | farm.safe |
View Guide: NGINX Load Balancing |
| VMs and Containers | Replication and Failover | Hyper-V | hyperv.safe |
View Guide: Hyper-V VM Replication |
| VMs and Containers | Replication and Failover | KVM | kvm.safe |
View Guide: KVM VM Replication |
| VMs and Containers | Replication and Failover | Docker | mirror.safe |
View Guide: Docker Container Failover |
| VMs and Containers | Replication and Failover | Podman | mirror.safe |
View Guide: Podman Container Failover |
| VMs and Containers | Replication and Failover | Kubernetes K3S | k3s.safe |
View Guide: Kubernetes K3S Replication |
| AWS Cloud | Real-Time Replication and Failover | AWS | mirror.safe |
View Guide: AWS Replication Cluster |
| AWS Cloud | Network Load Balancing and Failover | AWS | farm.safe |
View Guide: AWS Load Balancing Cluster |
| GCP Cloud | Real-Time Replication and Failover | GCP | mirror.safe |
View Guide: GCP Replication Cluster |
| GCP Cloud | Network Load Balancing and Failover | GCP | farm.safe |
View Guide: GCP Load Balancing Cluster |
| Azure Cloud | Real-Time Replication and Failover | Azure | mirror.safe |
View Guide: Azure Replication Cluster |
| Azure Cloud | Network Load Balancing and Failover | Azure | farm.safe |
View Guide: Azure Load Balancing Cluster |
| Physical Security / VMS | Real-Time Replication and Failover | Milestone XProtect | milestone.safe |
View Guide: Milestone XProtect Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Nedap AEOS | nedap.safe |
View Guide: Nedap AEOS Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Genetec (SQL Server) | sqlserver.safe |
View Guide: Genetec SQL Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Bosch AMS (Hyper-V) | hyperv.safe |
View Guide: Bosch AMS Hyper-V Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Bosch BIS (Hyper-V) | hyperv.safe |
View Guide: Bosch BIS Hyper-V Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Bosch BVMS (Hyper-V) | hyperv.safe |
View Guide: Bosch BVMS Hyper-V Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Hanwha Vision (Hyper-V) | hyperv.safe |
View Guide: Hanwha Vision Hyper-V Failover |
| Physical Security / VMS | Real-Time Replication and Failover | Hanwha Wisenet (Hyper-V) | hyperv.safe |
View Guide: Hanwha Wisenet Hyper-V Failover |
| Siemens Products | Real-Time Replication and Failover | Siemens Siveillance suite (Hyper-V) | hyperv.safe |
View Guide: Siemens Siveillance HA |
| Siemens Products | Real-Time Replication and Failover | Siemens Desigo CC (Hyper-V) | hyperv.safe |
View Guide: Siemens Desigo CC HA |
| Siemens Products | Real-Time Replication and Failover | Siemens Siveillance VMS | SiveillanceVMS.safe |
View Guide: Siemens Siveillance VMS HA |
| Siemens Products | Real-Time Replication and Failover | Siemens SiPass (Hyper-V) | hyperv.safe |
View Guide: Siemens SiPass HA |
| Siemens Products | Real-Time Replication and Failover | Siemens SIPORT (Hyper-V) | hyperv.safe |
View Guide: Siemens SIPORT HA |
| Siemens Products | Real-Time Replication and Failover | Siemens SIMATIC PCS 7 (Hyper-V) | hyperv.safe |
View Guide: SIMATIC PCS 7 HA |
| Siemens Products | Real-Time Replication and Failover | Siemens SIMATIC WinCC (Hyper-V) | hyperv.safe |
View Guide: SIMATIC WinCC HA |