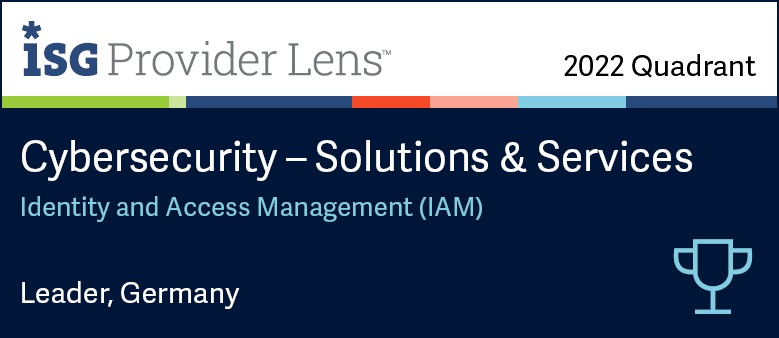
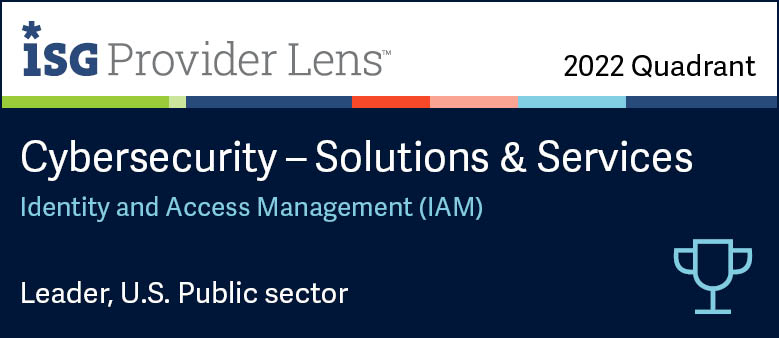
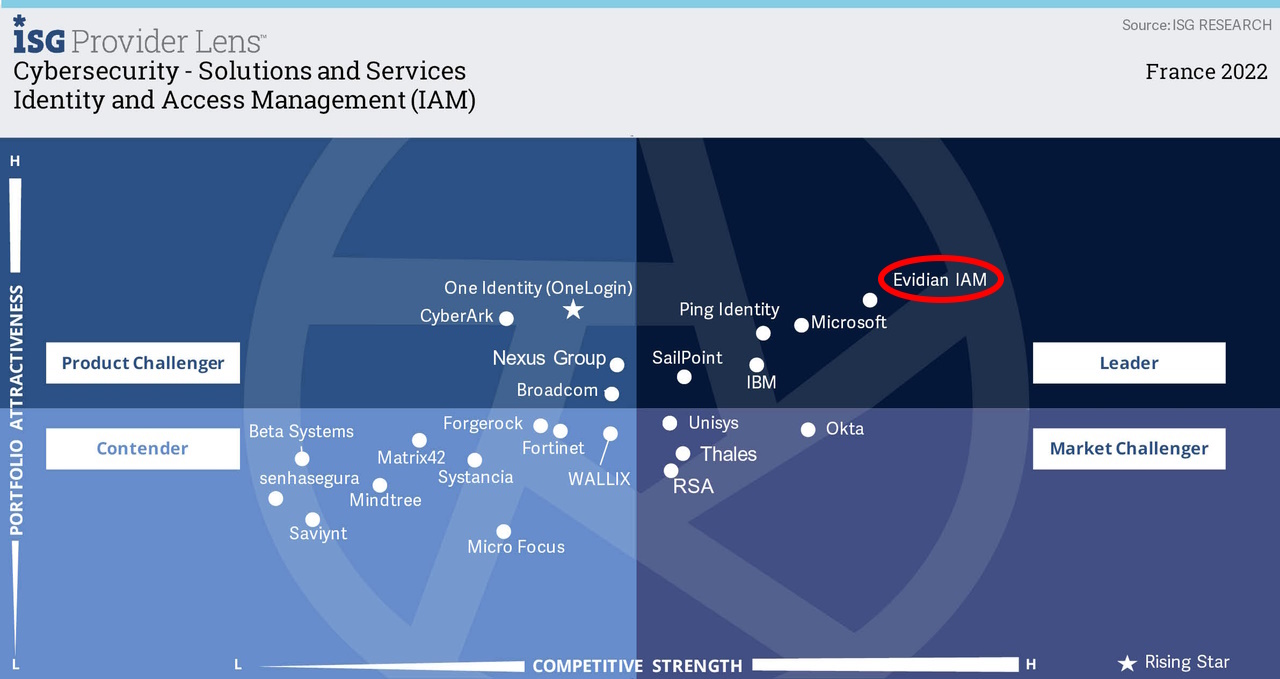
Overview of the Evidian Enterprise SSO engine
How does the Enterprise SSO engine is working with your applications?
Demonstration of the Enterprise (Single-Sign On) engine
With Evidian Enterprise SSO, a user enters a single password or even none with a strong authentication method. After that, application passwords are automatically entered, on behalf of the user.
Evidian comes with an SSO engine that detects login prompts from applications, whether web-based, desktop or legacy applications.
This video shows how the SSO engine allows the user to:
- Control the state of his E-SSO
- Launch his applications registered in E-SSO
- Manage the passwords of his applications
- Access personal notes protected by his E-SSO password
- Consult his Audit trail
- Configure his profile and access points
Why over 5 million employees are using Evidian Enterprise SSO today?
Reinforce access to applications
A user enters only one password or even none with Evidian Authentication Manager and a strong authentication method. Evidian SSO can change transparently hardened passwords for each application. It allows the management of enterprise access policies (which user can access to which application) and centrally audit the user access.
Reduce up to 30% helpdesk calls
There are no more calls to the call desk to reset passwords because users no longer manage application passwords. Moreover, a Self-Service Password request (SSPR) function allows users who have forgotten their single password, or their access card, to unlock their accesses - even offline without the helpdesk.
Never reveal passwords
Users can share the same generic accounts securely, or delegate their access to each other while being away. Users don’t need to reveal their passwords and are audited by name. Thanks to a web portal, a user who is already on leave can remotely delegate all or part of his accounts, via a simple web page and fully comply with the security policy.
Satisfy regulatory constraints
By creating an obligatory passage point between a user and his applications, an organization can effectively control the accesses. Moreover, a log of these accesses and administration operations is kept centrally, which facilitates audit. Evidian SSO facilitates compliance with confidentiality, integrity and availability requirements.

Evidian Enterprise SSO provides single sign-on to all users, businesses and organizations.
Free your users from remembering and typing passwords and drive your security policy by automating password management.
Examples of single sign-on solutions with Evidian Enterprise SSO and Authentication Manager
Typical use of SSO by over 5 million employees
Employees use a passwordless strong authentication method. After that, application passwords are automatically entered, on behalf of the employee, during application login prompts. This works either with web based, desktop as well as legacy applications without modifying them. Evidian gives an access to the applications to which the employee is entitled. And it transparently modifies and manages strong passwords for each application. An access log is centralized to facilitate audits, to know which employee uses which application and to meet regulatory constraints.
One PC - used by several users
Branch employees, sales staff in outlets, workers in manufacturing industry and others share a same PC in their Enterprise. They use a shared account with autologon to access the Windows session without password to save time. However, knowing who authenticated to the PC and at what time cannot be audited. Evidian with its multi-user desktop solves this problem with a fast user switching in a few seconds and a strong authentication method like a RFID badge to unlock the shared session.
One user – using multiple PCs successively
The day-to-day tasks of some employees may require them to move around within a site, such as doctors in a hospital, production managers at an industrial site, store vendors, and others. On each PC, they must log in to access their session and log out. As it takes time, an alternative solution must be found. Evidian offers a simple solution with a roaming session avoiding multiple login.
One user – using multiple PCs at once
Some employees need multiple PCs and monitors in order to work. These may include trading room workers, control room operators in industry, in transport, in video surveillance and others. It is unrealistic to ask these employees a multiple login to all PCs. Evidian offers a solution with a single login to multiple computers at once.
Are you looking for another solution?
Evidian offers many other solutions that will certainly meet your needs. Do not hesitate to contact us.
Passwordless, contactless, handsfree authentication

Evidian Authentication Manager replaces passwords by strong authentication methods.
Cover all authentication scenarios, whether a user accesses one or several PCs, or several users share one PC.
The three architectures of Single Sign-On
Enterprise directory (best architecture)
This is the architecture of Evidian Enterprise SSO. SSO information is simply stored, in encrypted form, in the directory that already equips most companies, guaranteeing a high level of confidentiality with non-reversible AES256 encryption. For example: the Microsoft Active Directory where users are declared and through which they access their Windows session; or its Microsoft AD-LDS application instance in which application data associated with users declared in the Active Directory. There is therefore no server or appliance to install. Your workstations are already configured to access the information, since they already access the directory.
SSO server
The information is stored on a server, for instance a Windows or Unix server, that is generally dedicated to this task. The client on the PC queries the server whenever necessary. This server is often duplicated for high availability, although cache mechanisms on the PC can compensate for temporary unavailability. Therefore, start-up costs must be taken into account: servers (but you can dedicate an existing server) and software installation. In a distributed architecture, the number of these servers may be high.
SSO appliance
It is just a variation of the SSO server solution: software and hardware are packaged together. Software-deployment costs are thus reduced. On the other hand, it is not possible to install the software on an existing server, which may increase the deployment costs. Finally, it is often impossible to add memory and disk on an appliance, unlike a server.
Orbion
Evidian takes care of everything related to your Identity and Access Management with Orbion (Identity as a Service)
Learn more >
Identity Governance and Administration
Manage access and authorization of all your users in your company
Learn more >
Web Access Manager
Gateway for web apps with SSO, multi-factor authentication, identity federation
Learn more >
Authentication Manager
Authentication Manager
Enterprise multi-factor & passwordless authentication on Windows PCs
Learn more >
Enterprise Single Sign-On (SSO)
Secure access to legacy and web apps on PCs & mobiles with SSO